Automatically deflect Zendesk spam tickets via triggers and webhooks
From time to time spammers use open API endpoint in Zendesk to flood your inbox with tickets. This article shows an efficient and automatic way to deflect these tickets.
For anyone using Zendesk in the last few days, the image below will be very familiar. All of the sudden your inbox gets flooded with spam tickets. They seem to originate from the web widget channel and contain Chinese characters.
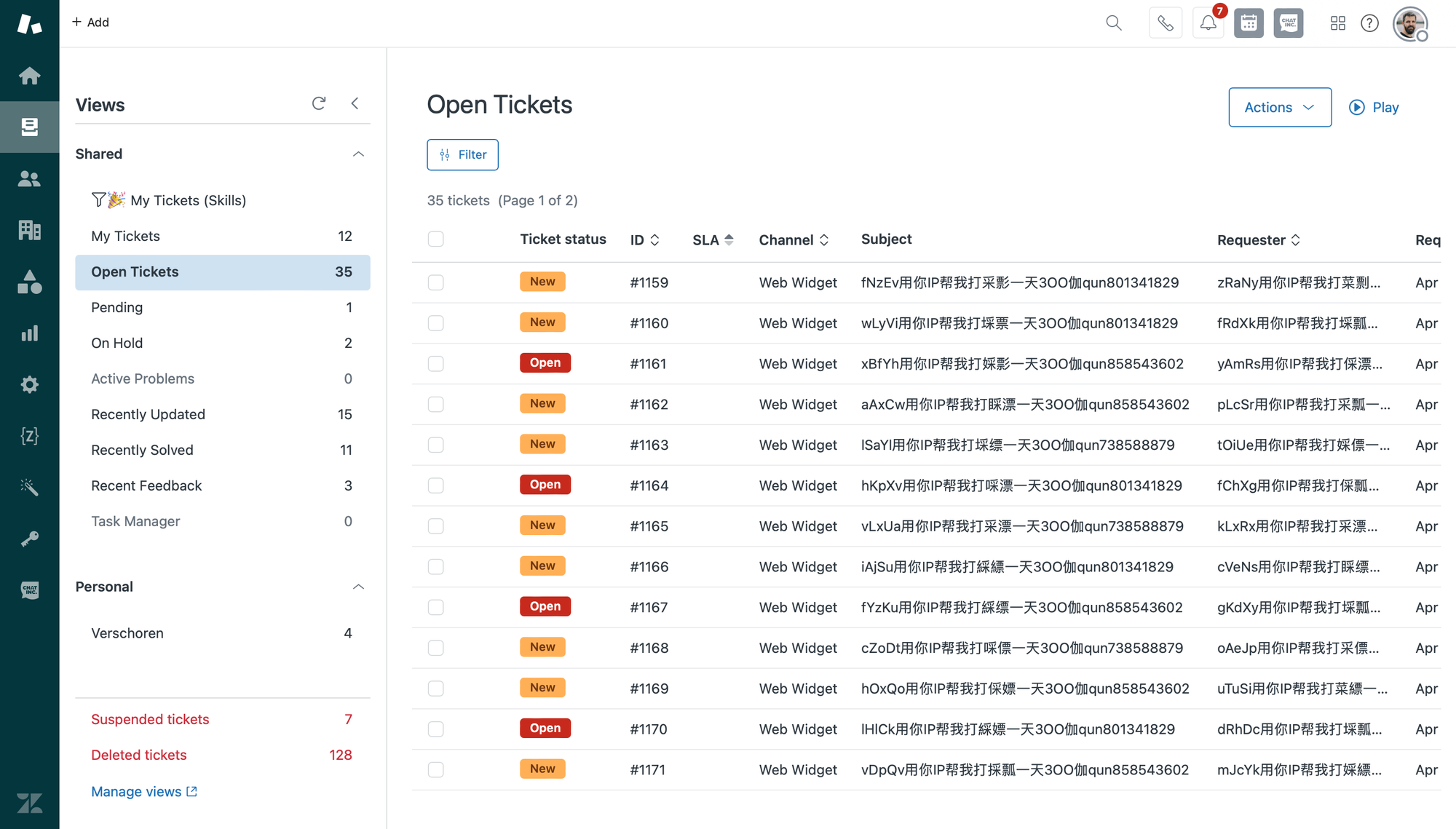
From what I can gather, and confirmed via other people contacting Zendesk, these tickets are created by spammers misusing the unauthenticated api/v2/requests/ endpoint that's used to create tickets via webforms.
Preventing these tickets is not really possible since the only way to close the endpoint is to prevent unauthenticated users from creating tickets, but that kinda defeats the purpose of having a Help Desk.
Zendesk always finds a way to deflect this spam-attacks by adapting their firewall and content filter settings, but in the meanwhile, here's an easy method to handle these tickets.
How to automatically mark tickets as spam.
Step 1: Identifying the tickets
Any automatic filter can only work as long as you find a way to identify the tickets. In this scenario there's two approached I took:
First I created an organization QQ that has a linked domain qq.com, since that's used by most of these requesters.
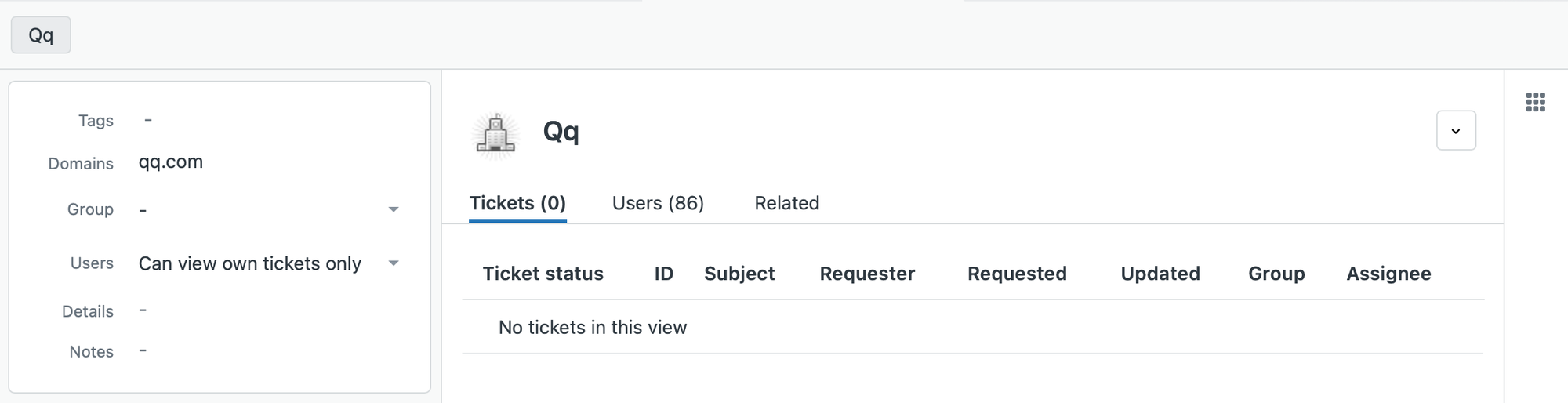
Secondly I noticed that all these tickets have a similar structure in their subject oZxQh用你IP帮我打婇嘌每天3OO伽qun858543602 so I can also use this to identify them.
Step 2: Webhook
Zendesk has an endpoint to mark tickets as spam and suspend end-users which is documented here.
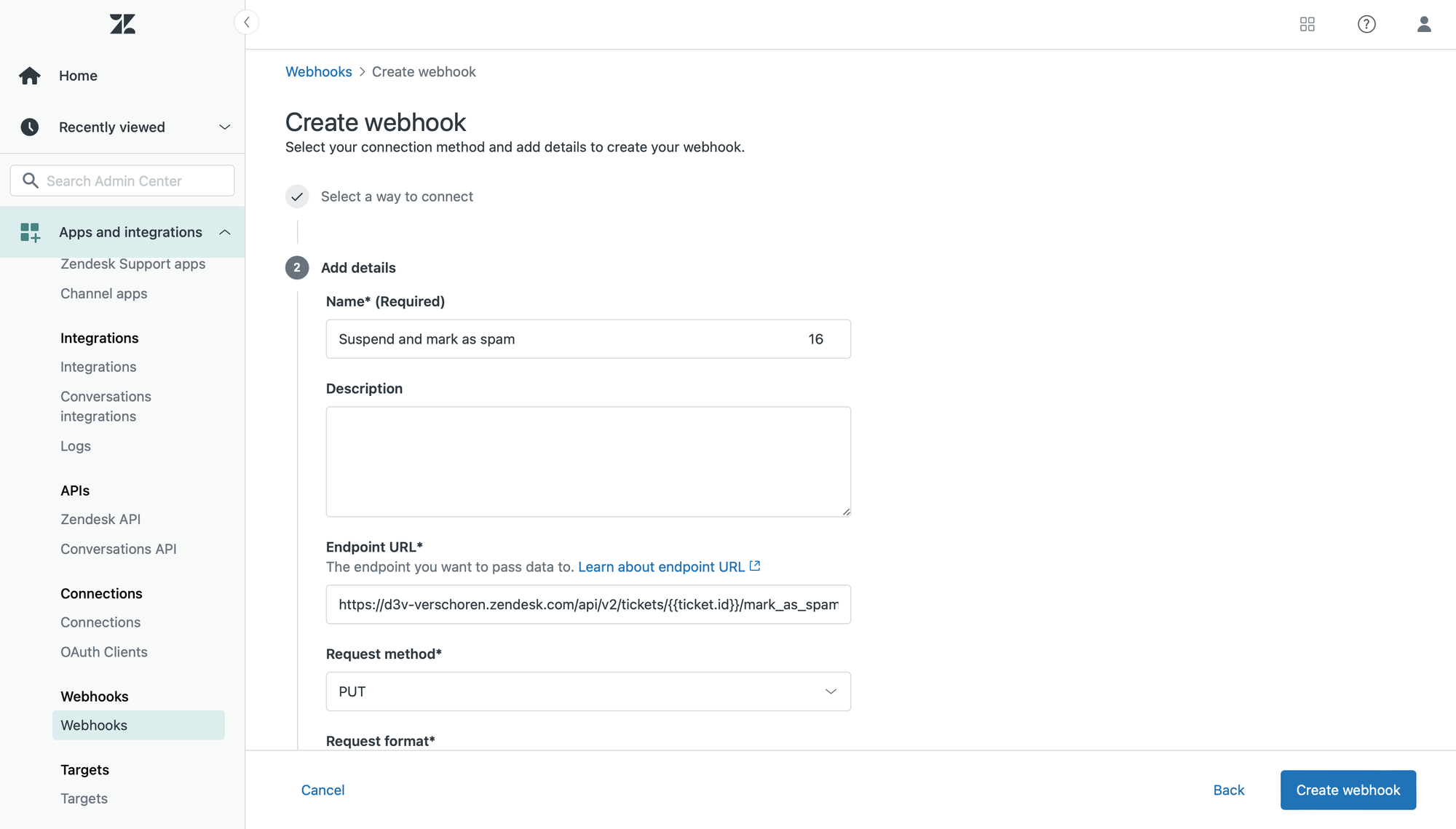
In order to automatically call this endpoint and mark tickets as spam, we'll need to create a webhook.
- Go to the admin center and navigate to Apps and integrations > webhooks
- Add a new web hook with
https://subdomain.zendesk.com/api/v2/tickets/{{ticket.id}}/mark_as_spamas the Endpoint URL and set the Request Method toPUT. - Authenticate with Basic Authentication with
[email protected]/tokenas the username and a Zendesk API token as the password.
Step 3: Trigger
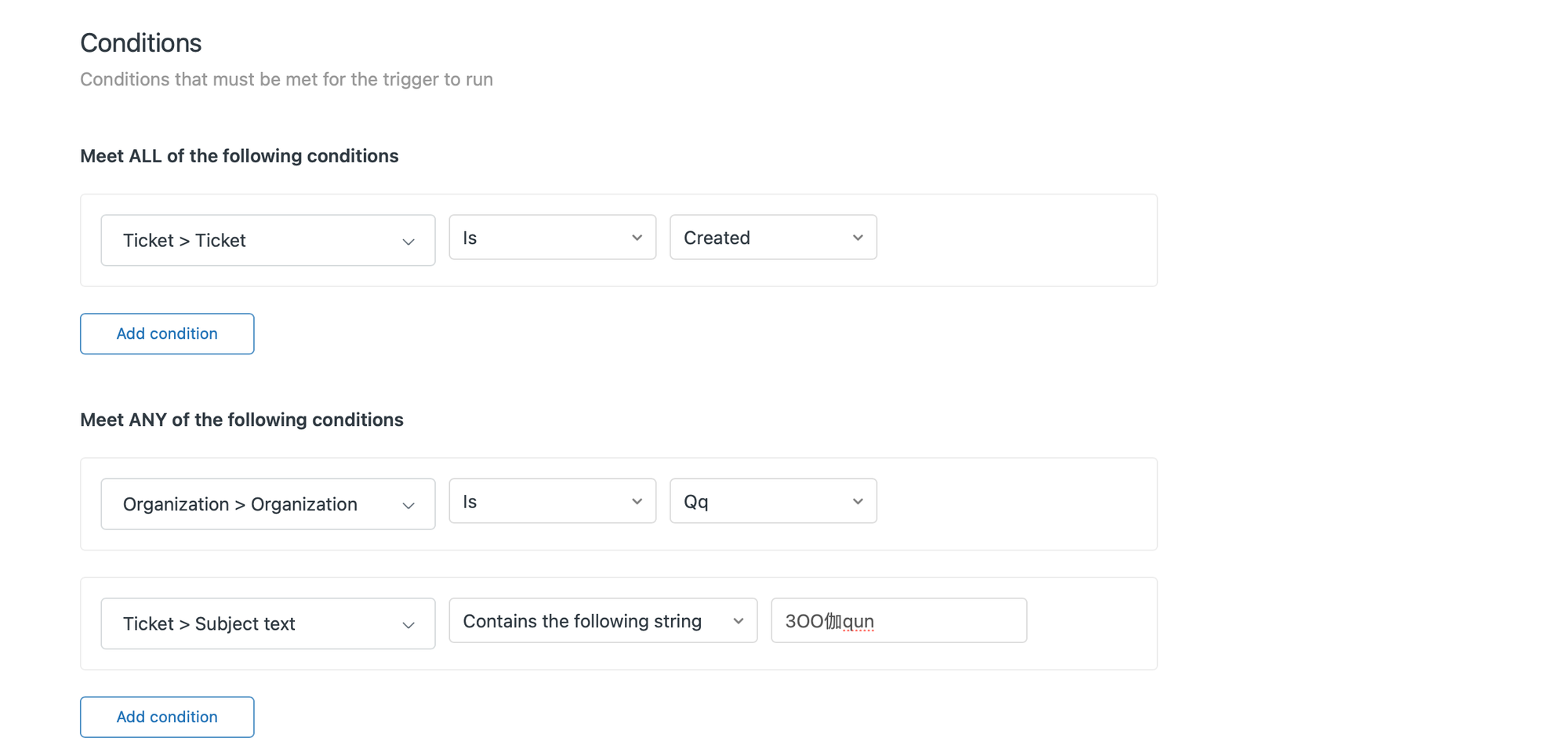
Finally, we'll need a trigger that will call the web hook if a potential SPAM ticket is created.
For the conditions, you can use the identifiers we defined in step 1:
- ALL: Tickets are created
- ANY:
- Organization is
Qq - Subject Text contains
3OO伽qun - (add your own)
- Organization is
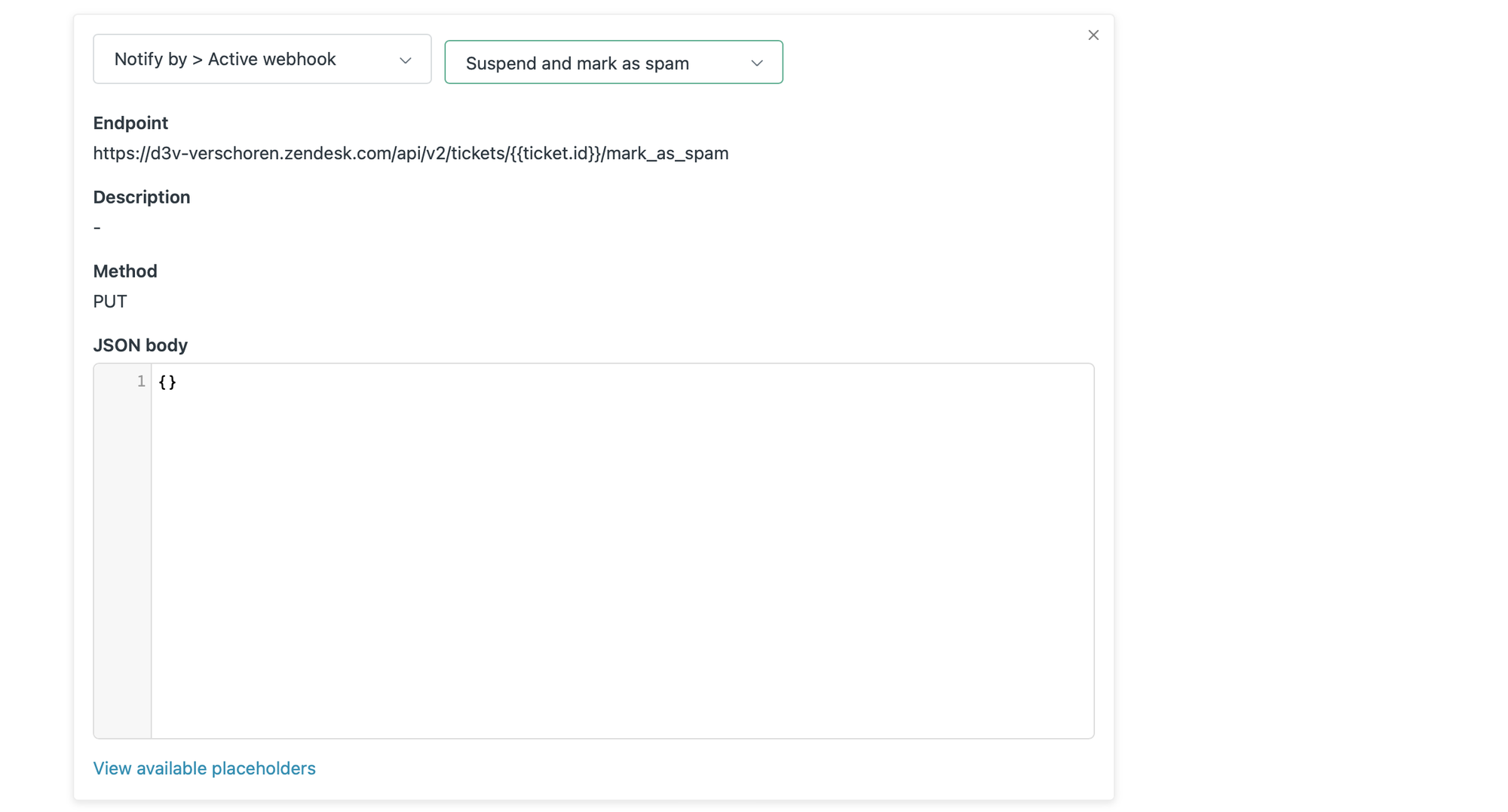
And for the actions, select the webhook we just created. You can leave the JSON body empty or leave the {} that's added by default.
Wrap up
Any new tickets that fall under your spam rules will now be automatically marked as spam and be suspended, no longer filing your views.
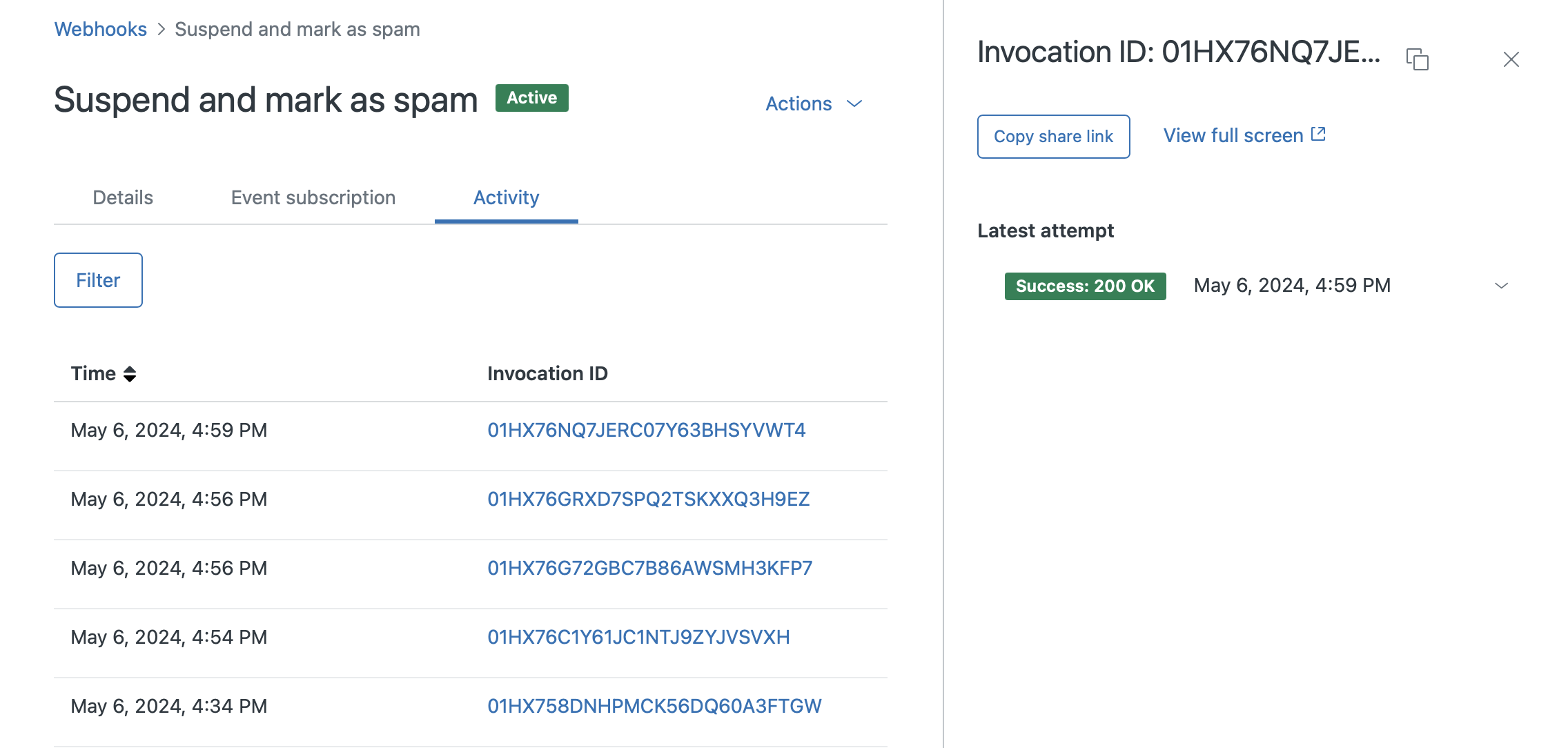
You can follow the suspensions executed by looking at the Activity tab of your webhook's configuration page in the Admin Center. Each successful suspension will be market with a Success:200 OK status.
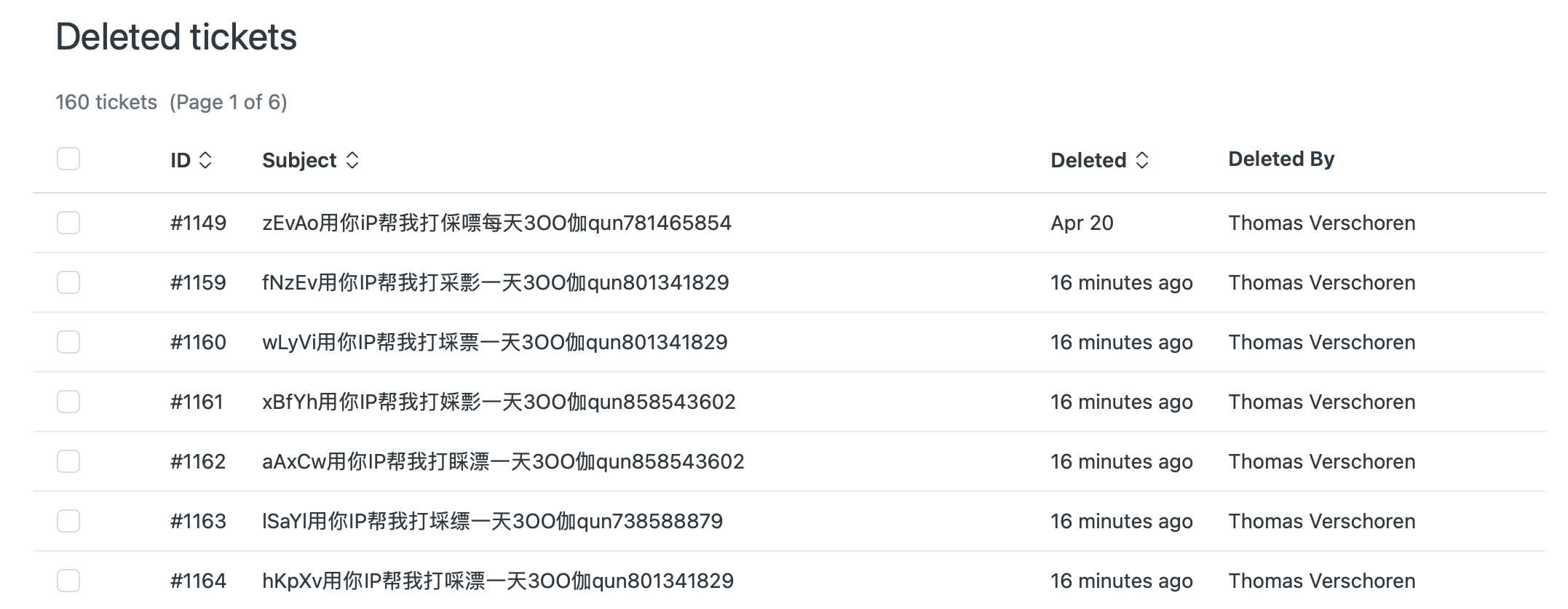
And if you check your Deleted or Suspended Tickets views, you'll be greeted with a list of tickets.
The only real maintenance here is that to keep an eye on spammers using some new format and updating your trigger accordingly.